Aes Key And Iv Generator
PROGRAMMING INTERFACE
AES-CBC (cipher block chaining) mode is one of the most used symmetric encryption algorithms. The data size must be nonzero and multiple of 16 bytes, which is the size of a “block”. The data is split into 16-byte blocks before encryption or decryption is started, then the operation is performed on each of the blocks.
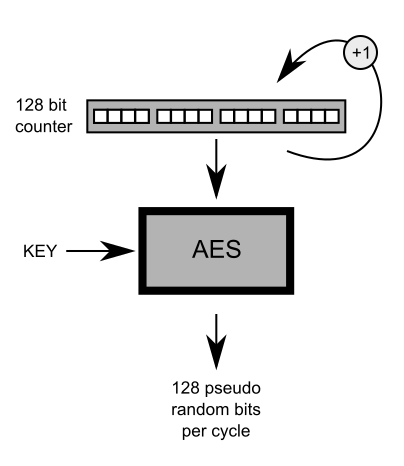
- Mar 17, 2017 Generate a random IV for each message (using a cryptographic-quality random generator, the same you'd use to generate a key), and you'll be fine. There is one exception: if you generate a fresh key for each message, you can pick a predictable IV (all-bits 0 or whatever).
- AES encryption is a web tool to encrypt and decrypt text using AES encryption algorithm. The tool is free, without registration.
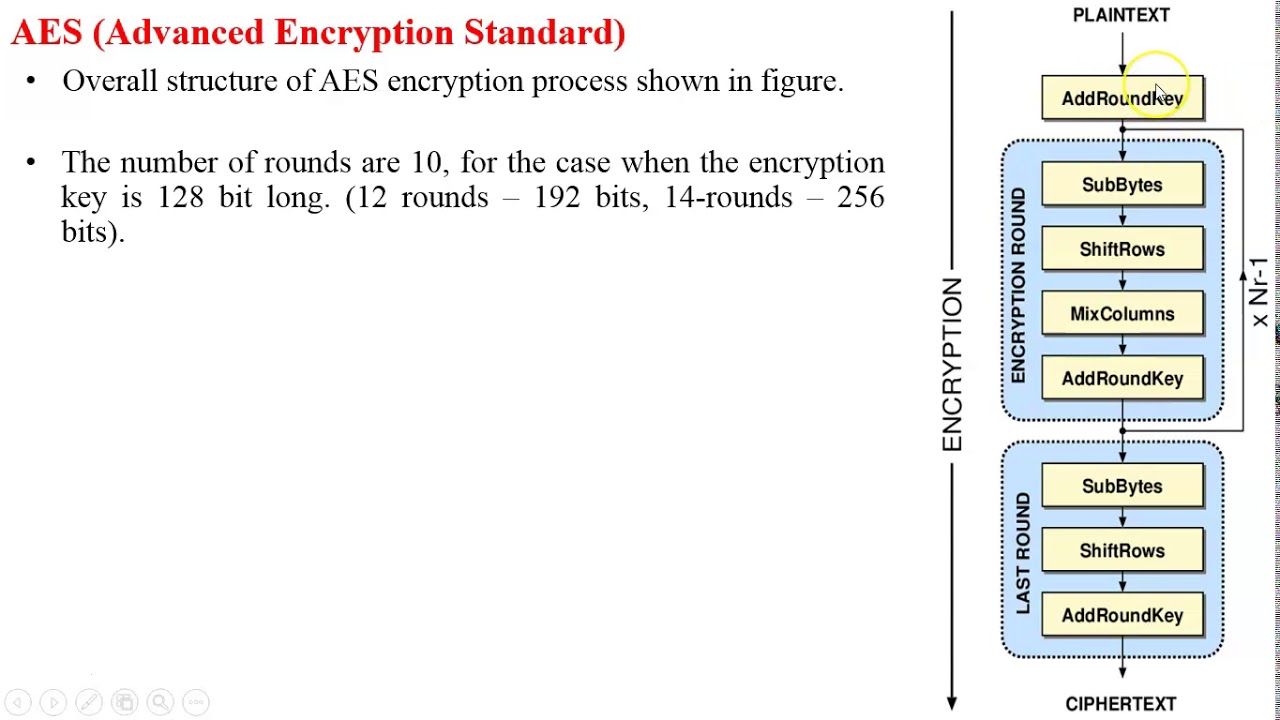
- AES (acronym of Advanced Encryption Standard) is a symmetric encryption algorithm. The algorithm was developed by two Belgian cryptographer Joan Daemen and Vincent Rijmen. AES was designed to be efficient in both hardware and software, and supports a block length of 128 bits and key lengths of 128, 192, and 256 bits.
- The AES encryption is a symmetric cipher and uses the same key for encryption and decryption. The AES algorithm supports 128, 192 and 256 bit encryption, whi.
Internal state is maintained in an opaque structure that is returnedfrom the Init function. In ECB mode the state is not affected bythe input but for CBC mode some input dependent state is maintainedand may be reset by calling the Reset function with a newinitialization vector value.
Construct a new AES key schedule using the specified key data and thegiven initialization vector. The initialization vector is not usedwith ECB mode but is important for CBC mode.See MODES OF OPERATION for details about cipher modes.
Use a prepared key acquired by calling Init to encrypt theprovided data. The data argument should be a binary array that is amultiple of the AES block size of 16 bytes. The result is a binaryarray the same size as the input of encrypted data.
Decipher data using the key. Note that the same key may be used toencrypt and decrypt data provided that the initialization vector isreset appropriately for CBC mode.
Reset the initialization vector. This permits the programmer to re-usea key and avoid the cost of re-generating the key schedule where thesame key data is being used multiple times.
This should be called to clean up resources associated with Key.Once this function has been called the key may not be used again.
Introduction to AES
The AES encryption is a symmetric cipher and uses the same key for encryption and decryption. The AES algorithm supports 128, 192 and 256 bit encryption, which is determined from the key size : 128 bit encryption when the key is 16 bytes, 192 when the key is 24 bytes and 256 bit when the key is 32 bytes.
The methods provided by the library accept also a string password instead of a key, which is internally converted to a key with a chosen Hash function.
The optional initialization vector (IV) size is 16 bytes, which is the block size of the algorithm. This is summarized in the table below:
| Key size | AES encryption |
| 16 bytes (128 bits) | 128 bit encryption |
| 24 bytes (192 bits) | 192 bit encryption |
| 32 bytes (256 bits) | 256 bit encryption |
| IV size:16 bytes |
Back to Top
Padding and Block modes
The Padding and Block mode are important settings for the AES class, that affect the produced encrypted output.
The Padding is used to align the input data to the algorithm BlockSize (16 bytes). The default is PKCS7.

The Block Mode determines what transformation is performed on each processed block. The default one is CBC. It is very important to know what block mode was used for encryption, in order to be able to decrypt it! For example if we know that the encryption has used CTR block mode, we shall set the class to use that mode before decrypting:
Back to Top
AES encrypting and decrypting a String
The example below shows how to AES encrypt and decrypt a String with a byte array key, with a password and by using or not the optional initialization vector (IV).
Back to Top
Encrypting and Decrypting a File
The file encryption is performed by calling the methods AES.EncryptFile. The decryption is through the DecryptFile methods respectively:
VB.NET example
Back to Top
AES Encrypting and decrypting a Stream
The Stream encryption is performed by reading the data from a Stream opened for reading and writing the encrypted output to a Stream that accepts write operations. After the method execution, the output Stream Position will be at the end of the encrypted data.
C# code
VB.NET code
Back to Top
Encrypting and Decrypting a Byte array
The EncryptBytes and DecryptBytes methods accept byte array as input and return the output as byte array. The example below demonstrates the four possibilities for AES key and initialization vector (IV) offered by the library:
C# example
Aes Key And Iv Generator Manual
VB.NET example
Back to Top
Exception handling
During the AES encryption and decryption operations errors can appear. In order to handle them more gracefully, the library offers a set of typed exceptions that can help us identify the cause of the error.
Below is an example class that demonstrates the various exceptions that can be expected during encryption and decryption. The methods that deal with files and streams of course may also throw System.IO.IOException sub classes:
C# code
VB.NET code
Summary
Aes Key And Iv Generator 2020
This chapter illustrated how to perform AES encryption and decryption with the help of NCiphers.Crypto library.